
| ||||||||||||||
|
| Reconfigurable Security with Reconfigurable Hardware From Bluetooth transceivers to the NASA Mars Rover, reconfigurable circuits (such as the one pictured below) have become one of the mainstays of embedded design. Combining the high computational performance of specialized circuits with the re-programmability of software, these devices are quickly becoming ubiquitous - unfortunately this hardware malleability can be twisted to disrupt critical operations, snoop on supposedly secure channels, or even to physically melt a device. The goal of our research is to enable a new class of systems that are both reconfigurable and secure. There are three important areas need to be addressed in order to achieve these goals: enforcing logic-level separation, advanced memory protection, and dynamic policy management. 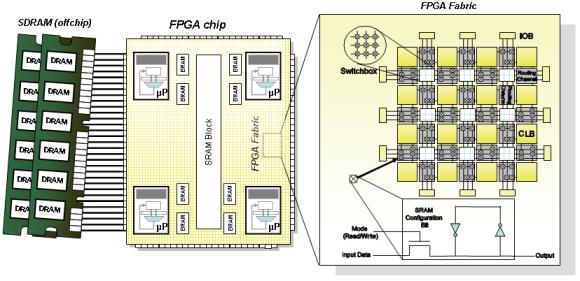 Dynamic Policy Management While reconfigurability creates problems as described above, it also creates opportunities: in particular the opportunity for hardware enforcement of adaptive security policies. In an emergency, trusted individuals may need to override the nominal security policy. The reconfigurable component may provide a highly trusted mechanism for secure functionality in changing environments. Thus a key aspect of our work is in establishing a firm foundation for trustworthy dynamic policy enforcement through ontological analysis and formal modeling. Advanced Memory Protection Virtual Memory is the mechanism by which many security policies are enforced, it is all but non-existent on embedded systems. While a TLB-like structure could be constructed out of the logic blocks that populate a modern reconfigurable device, instead we need to rethink the way that embedded memory is protected and shared. With reconfigurable hardware we can implement test example enforcement mechanisms and reason formally as to their security. Logic Protection and Interface Enforcement The problem does not stop at memory management. In reconfigurable systems the logic of the hardware can be changed, which opens a host of problems that have no easy analogs in the software domain. For example, configurations can be loaded that cause short circuits or even meltdown. Secret data may need to share the same chip as untrusted intellectual property which has the potential to improperly impede or probe the device. New methods are needed that can statically validate these configurations.
|
| ||||||||||||


